Qiaoling Long
Secure Storage of Network Data Information Based on Cloud Computing Data Encryption Techniques
Abstract: In a cloud computing environment, frequent data interactions require high information security. This paper briefly overviews encrypted data storage in the cloud computing environment. A dual encryption scheme that combined identity attributes and security devices was proposed. The scheme was evaluated through simulation experiments conducted on a laboratory server. The results indicated that an increase in the size of the storage file led to an increase in the time overhead of the encryption scheme. Furthermore, the dual encryption scheme exhibited slightly higher time overhead than a single security device encryption scheme, but was similar to a single identity attribute-based encryption scheme. For cloud storage data, the successful queries of encrypted data and effective resistance against third-party attacks were only achieved when the number of overlapping identity attributes was 5, which was the same as the storage user.
Keywords: Cloud Computing , Data Encryption , Data Storage , Dual Encryption
1. Introduction
Traditional data processing, storage, and other operations are typically performed on local computers, and their performance depends on these computers' capabilities [1]. However, there are limitations to the configuration of local computers. There is a marginal effect between the cost of computer configuration and its performance. After reaching a certain level of performance, the cost required to achieve the same degree of performance enhancement will be higher [2]. Cloud computing technology has emerged to overcome these limitations and enhance computing performance. Cloud computing utilizes the Internet to connect multiple computers and collaboratively solve problems in parallel. Cloud computing can achieve higher performance by pooling the computational power of these computers. Theoretically, there is no upper limit to the computational power that can be obtained by expanding the size of computer nodes in cloud computing. However, in practice, there are limits imposed by the construction of cloud computing nodes and the speed of internet data transmission [3]. Therefore, the enhancement of computational power in cloud computing has a marginal effect, but it surpasses the computational power of local computers. In addition, cloud computing requires data exchange over the Internet when aggregating computational power from multiple computer nodes, which exposes the computation data to the Internet and poses risks to data security, including data leakage risks caused by deficiencies in aspects such as access permission control, key generation, storage, and management, data damage risks resulting from vulnerabilities in the sharing mechanism of cloud computing platforms, and account hijacking risks. The above-mentioned security risks will all lead to the leakage of data transmitted and stored in the cloud computing platform. If the data contains sensitive information, the losses caused will be further increased. Therefore, it is necessary to encrypt the data to reduce the risks. Wei et al. [4] proposed the concept of revocable storage identity-based encryption, which provides forward/backward security of ciphertexts through user revocation and ciphertext updating functions. Zhang et al. [5] put forward an online/offline multi-authority attribute-based encryption scheme that supports a fully large attribute universe while enabling online/offline key generation and encryption. Reddy et al. [6] developed a framework combining encryption with access policy enforcement and cloud data selection to enhance the security and efficiency of cloud computing systems. Dewangan et al. [7] utilized homomorphic encryption to solve the problem of visible spectral image encryption. Agrawal and Sharma [8] put forward an encryption algorithm based on a symmetric algorithm, which used the user end and cloud storage to encrypt and decrypt data to protect information from various attackers. Akshay et al. [9] combined the complex binary search tree structure with elliptic curve encryption technology in the cloud storage system, which not only ensures efficient data retrieval but also ensures a robust encryption mechanism. The above-mentioned related studies have all conducted analysis and research on cloud storage and data encryption. Some start from the perspective of data encryption, and some from the perspective of secure retrieval of stored data. This paper focused on the secure encryption of data in the cloud computing platform and used identity attributes and security devices to achieve double encryption of data to further enhance the security of stored data. This paper briefly introduces the encrypted data storage in a cloud computing environment. A dual encryption scheme based on identity attributes and security devices was developed and evaluated through simulation experiments conducted on a laboratory server. The novelty of this paper lies in encrypting the data in the cloud computing platform from perspectives of identity attributes and security devices, which improves the data security. The limitation of this paper is that although the double encryption of data by using identity attributes and security devices guarantees security, it also increases the computing overhead of the entire system and reduces the efficiency of cloud computing. Therefore, the future research direction is to reduce the overhead of data encryption on the basis of ensuring security.
2. Data Encryption in a Cloud Computing Environment
Cloud computing technology leverages the connectivity of the Internet to integrate multiple computer nodes, thereby significantly enhancing computational power. However, cloud computing necessitates transmitting data among different computer nodes through the Internet [10], which introduces the risk of data leakage.
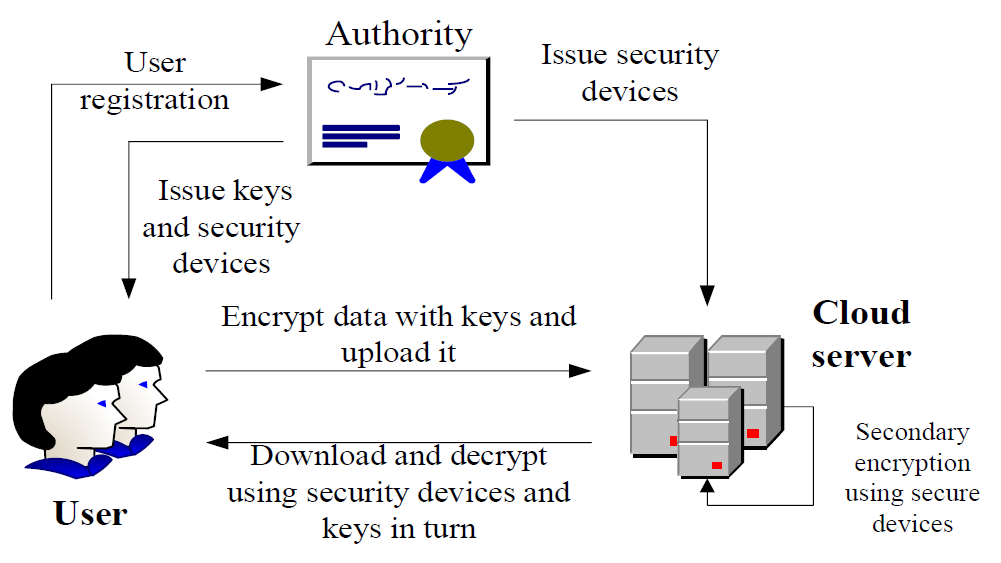
The data encryption storage model based on the cloud computing environment is presented in Fig. 1. The whole model is mainly composed of an authority, users, and a cloud server [11]. The authority is a third-party trusted organization in the whole cloud computing service, responsible for generating the parameters required for the encryption scheme and the management of user information. Users are customers of the cloud computing service, which can be either the provider of the stored data or the receiver of the stored information [12]. The cloud server end provides the cloud computing service for users and stores the data uploaded by users. In the encryption and storage process, the authority generates the relevant key according to the user's registration information, the user uses the key to encrypt the data once, the cloud service end carries out the secondary encryption and then stores it, and the user downloads the ciphertext from the cloud server and then decrypts it using the key to obtain the plaintext data. The specific steps are shown below.
1) The authority computes the public parameter and master key by algorithm G [13]. The public parameter and master key are
(1)
[TeX:] $$\left\{\begin{array}{l} m s k=\left(y, t_1, \cdots, t_n\right) \\ p k=\left(g^{t_1}, \cdots, g^{t_n}, Y=e(g, g)^y\right) \end{array}\right.$$where msk is the master key, pk is a public parameter, [TeX:] $$y \text { and } t_i$$ are random non-negative integers not exceeding p - 1, p is the order of the multiplicative cyclic group in an elliptic curve, g is the generator element of the multiplicative cyclic group [14], and [TeX:] $$t_i$$ is a random parameter representing the i-th attribute.
2) A new user registers in the authority and provides the authority with his/her identity information containing multiple attribute characteristics.
3) The authority utilizes the attribute features contained in the identity information provided by the user to generate the user's key [15]:
where sk is the private key given to the user, S is the set of identity attributes that the user has, [TeX:] $$D_i$$ is the private key of the i-th attribute (all the private keys of attributes belonging to S are combined to form sk), d is the threshold value, and p() is the d - 1-th polynomial function [16]. The security device uses the Data Encryption Standard (DES) encryption algorithm to encrypt the ciphertext again.
The DES algorithm is a symmetric encryption algorithm [11], which has high efficiency of encryption and decryption and is suitable for secondary encryption processing of many ciphertexts in the cloud. The principle of this algorithm is as follows. The plaintext is divided into left and right parts. Then, in each round of encryption iteration, the right part encrypted using a key and the left part are added up. The obtained result is exchanged with the right part. The step is repeated until the preset number of round is reached.
4) The authority sends sk to the corresponding user and sends the key of the DES algorithm to the user and the cloud server.
5) When the user uploads data to the cloud, the data is encrypted preliminarily using pk that the authority made public:
where [TeX:] $$C_1$$ is preliminary ciphertext, m is the plaintext, [TeX:] $$S^\prime$$ is the user's identity attribute, and s is a random non-negative integer not exceeding p−1. Then, the ciphertext is uploaded to the cloud.
6) After receiving the ciphertext, the cloud uses the key of the DES algorithm to encrypt the ciphertext again. In the secondary encryption, the ciphertext is regarded as plaintext, and then it is grouped into different groups, 32-bit long each group. A 32-bit plaintext is input, and i=0. Then, the plaintext is divided into 16-bit left data [TeX:] $$L_1$$ and 16-bit right data [TeX:] $$R_i$$. [TeX:] $$R_i$$ is directly used as left data [TeX:] $$L_{i+1}$$ after one round of encryption and encrypted by the round function and key [TeX:] $$k_i$$. Then, XOR operation is performed on the ciphertext and [TeX:] $$L_i$$ to obtain right data [TeX:] $$R_{i+1}$$ after one round of encryption. After 16 rounds of encryption, the left and right data are combined to form the encryption result, which is the secondary encrypted ciphertext. It is stored in the cloud.
7) The user downloads the stored ciphertext from the cloud and uses the key of the security device issued by the authority to decrypt the ciphertext for the preliminary decryption. The key is used in reverse order in the DES algorithm [17]. After the decryption, whether the number of overlapping authority identity attributes between S and [TeX:] $$S^\prime$$ is less than threshold value d is determined. If less than, it cannot be decrypted; otherwise, d attributes are arbitrarily taken out from the overlapping attributes, and [TeX:] $$e(g, g)^{p(i) s}=e\left(E_i, D_i\right)$$ is calculated, where i belongs to the d attributes arbitrarily taken. After that, the decryption formula is:
where [TeX:] $$e(g, g)^{p(0) s}$$ is calculated by Lagrange interpolation [15] combined with [TeX:] $$e(g, g)^{p(i) s}$$.
3. Simulation Experiments
3.1 Experimental Environment
The simulation experiment was carried out using four servers. Server 1 acted as an authority, responsible for user registration and the distribution of keys and security devices. Server 2 acted as a cloud server, responsible for cloud storage of data. Server 3 acted as a user, responsible for uploading and downloading data. Server 4 acts as an attacker to attack the stored data. All the four servers were configured with Windows 11 operating system, 16 G memory, and i7 processor.
3.2 Experimental Setup
Performance testing of the encryption algorithm: Firstly, 20 users were randomly generated from server 3, each with five different identity attributes. Then, the users registered on server 1 to obtain the key for preliminary encryption and the key for the security device. Afterward, each user sent files of sizes 0.01 MB, 0.1 MB, 1 MB, 10 MB, and 100 MB to the cloud server to test the time overhead and average latency time.
Additionally, for comparison, the time overhead and average latency time of encryption algorithms relying solely on preliminary encryption and relying solely on the security device were tested using the same users and sent files.
Use test of the encryption algorithm: After storing the data in the cloud, the users queried it and then downloaded and decrypted it to compare the query results between users with different numbers of overlapping identity attributes.
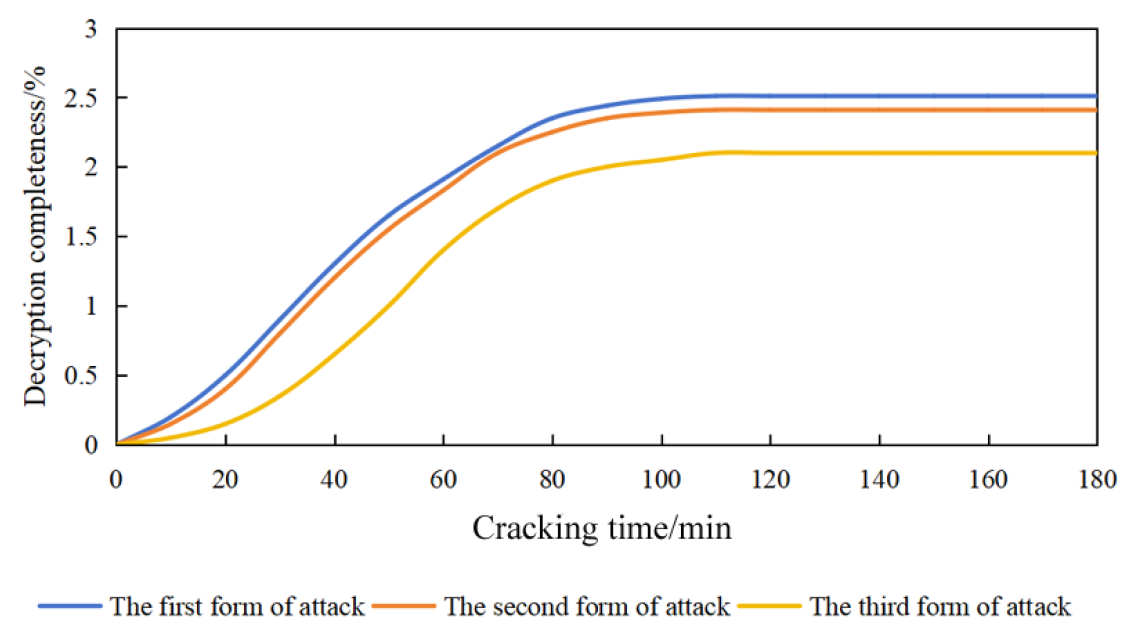
Security testing of the encryption algorithm: After the user sent a file to the cloud server for storage, server 4 decrypted it as an attacker. There were three forms of attack by the attacker: without the key of the security device but with the preliminary encryption key, without the preliminary encryption key but with the key of the security device, and without both the security device key and the primary encryption key. All three forms of attacks were attempted to decrypt the ciphertext.
3.3 Experimental Results
The time overhead and average latency time of the dual encryption algorithm proposed in this paper for encrypting files of different sizes were first tested and compared with the other two encryption schemes. It can be seen from Fig. 2 that the time overhead of the three encryption schemes increased as the file size increased. The encryption scheme relying only on the security device had the least time overhead for the same file size. In contrast, the preliminary encryption-only scheme and the proposed dual encryption scheme had more time overhead, and they were similar. As the file size increased, the average latency time of the three encryption schemes remained stable and then increased. For the same file size, the average latency time of the encryption scheme that relied only on the security device was the least. The average latency time of the preliminary encryption-only scheme and the dual encryption scheme was higher, and they were similar.
After that, the use of the dual encryption scheme was tested. Table 1 shows the success rate of querying the stored data using different numbers of overlapping identity attributes. Table 1 shows that, whether for text, audio, or video data, the successful query to the encrypted data was only possible when the number of overlapping identity attributes was 5, which was the same as the storage user. Even if only one identity attribute is not overlapped, the plaintext cannot be queried successfully.
Fig. 2.

Table 1.
| Data type | Number of overlapping identity attributes | |||||
|---|---|---|---|---|---|---|
| 0 | 1 | 2 | 3 | 4 | 5 | |
| File | 0% | 0% | 0% | 0% | 0% | 100% |
| Video | 0% | 0% | 0% | 0% | 0% | 100% |
| Audio | 0% | 0% | 0% | 0% | 0% | 100% |
Finally, the security of the dual encryption scheme was tested. The server acting as an attacker employed three attack forms to crack the data stored in the cloud server. It can be seen from Fig. 3 that as the cracking time increased, the decryption completeness of the stored ciphertexts under the three attack forms first rose and then tended to stabilize. This meant the data leakage caused by the three attack forms was limited, and the dual encryption scheme could resist attacks from third parties. After the decryption completeness tended to stabilize, the decryption completeness of the third attack form was the lowest, while the decryption completeness of the first form was the highest. This is because the third attack form without the key of the security device and the key of the preliminary encryption faced the double-encrypted ciphertexts. In contrast, the first and second attack forms each had one key, and they only needed to face the single-encrypted ciphertexts, so their decryption completeness was higher. Additionally, the first attack form that only had the key for the security device needed to decrypt the ciphertext processed by preliminary encryption. The second attack form only had the key for preliminary encryption needed to decrypt the ciphertext of the security device. The DES algorithm adopted by the security device is a symmetric encryption algorithm that is easier to crack compared to the ciphertext processed by preliminary encryption.
4. Discussion
In the current digital era, data has become the core asset for the development of enterprises and society. With the popularization of the Internet and the development of information technology, the amount of network data information has grown explosively. However, along with the increase in data volume, security issues such as data leakage and privacy infringement have become increasingly prominent, becoming a major obstacle restricting enterprises and individuals from utilizing network resources. Cloud computing, as an emerging information technology mode, provides users with an efficient and convenient solution for data processing and storage with its powerful computing capabilities and flexible service mode. However, despite the many conveniences brought by cloud computing, the security challenges it faces cannot be ignored. Especially in the field of data encryption, due to the openness and sharing nature of the cloud environment, traditional encryption schemes are difficult to meet users' high requirements for data confidentiality. This paper selected a dual encryption scheme based on identity attributes and security devices to encrypt data in the cloud environment. Then, experiments were conducted in the simulated cloud environment built on the laboratory server. Although the dual encryption scheme of identity attributes and security devices had slightly more time cost and average latency time, it was more excellent in encryption performance and was more capable of resisting third-party attacks. The reason is that in the encryption scheme based on security devices, the DES encryption algorithm was used. The encryption scheme based on security devices and identity attributes required secondary encryption, so the efficiency of encryption and decryption was lower. In terms of data protection, in the encryption scheme that solely relied on security devices, it is also because the DES algorithm was relatively easier to crack. However, the dual encryption scheme adopted in this paper not only used identity attributes to perform asymmetric encryption on the plaintext but also used the DES algorithm to perform secondary encryption on the ciphertext, so it was more secure.
5. Conclusion
This paper briefly introduces the encrypted data storage in the cloud computing environment. A dual encryption scheme incorporating identity attributes and security devices was adopted. The scheme was evaluated through simulation experiments conducted on laboratory servers. The encryption scheme solely based on security devices demonstrated the lowest time overhead and average latency time. On the other hand, the encryption scheme based solely on identity attributes and the dual encryption scheme both had higher time overhead and average latency time, with little difference between them. For the data stored in the cloud server, successful retrieval was only possible when there were five overlapping identity attributes, i.e., the same as the storage user. In other words, if there is no overlap in even one identity attribute, the plaintext of the encrypted data cannot be queried. The dual encryption scheme could effectively resist attacks from third parties.
Biography
Qiaoling Long
https://orcid.org/0009-0009-7883-8851She was born in June 1979, graduated from South China Agricultural University with a master’s degree in June 2013. She is working at Guangdong Polytechnic of Science and Technology. Her professional titles are experimentalist and senior information system project manager. She is interested in cloud computing technology and blockchain technology.
References
- 1 V . Arora, and S. S. Tyagi, "Analysis of symmetric searchable encryption and data retrieval in cloud computing," International Journal of Computer Applications, vol. 127, no. 12, pp. 46-51, 2015. https:// doi.org/10.5120/ijca2015906567doi:[[[10.5120/ijca906567]]]
- 2 S. Xue, and C. Ren, "Security protection of system sharing data with improved CP-ABE encryption algorithm under cloud computing environment," Automatic Control and Computer Sciences, vol. 53, no. 4, pp. 342350, 2019. https://doi.org/10.3103/S0146411619040114doi:[[[10.3103/S014641160114]]]
- 3 V . Kulshrestha, S. Verma, and C. R. Krishna, "Hybrid probabilistic triple encryption approach for data security in cloud computing," International Journal of Advanced Intelligence Paradigms, vol. 21, no. 1-2, pp. 158-173, 2022. https://doi.org/10.1504/IJAIP.2022.121035doi:[[[10.1504/IJAIP.2022.15]]]
- 4 J. Wei, W. Liu, and X. Hu, "Secure data sharing in cloud computing using revocable-storage identity-based encryption," IEEE Transactions on Cloud Computing, vol. 6, no. 4, pp. 1136-1148, 2018. https://doi.org/ 10.1109/TCC.2016.2545668doi:[[[10.1109/TCC.2016.2545668]]]
- 5 Y . Zhang, D. Zheng, Q. Li, J. Li, and H. Li, "Online/offline unbounded multi‐authority attribute‐based encryption for data sharing in mobile cloud computing," Security and Communication Networks, vol. 9, no. 16, pp. 3688-3702, 2016. https://doi.org/10.1002/sec.1574doi:[[[10.1002/sec.1574]]]
- 6 M. I. Reddy, P. V . Rao, T. S. Kumar, and K. S. Reddy, "Encryption with access policy and cloud data selection for secure and energy-efficient cloud computing," Multimedia Tools and Applications, vol. 83, no. 6, pp. 15649-15675, 2024. https://doi.org/10.1007/s11042-023-16082-6doi:[[[10.1007/s11042-023-16082-6]]]
- 7 R. R. Dewangan, S. Soni, and A. Mishal, "Optimized Homomorphic Encryption (OHE) algorithms for protecting sensitive image data in the cloud computing environment," International Journal of Information Technology, vol. 16, no. 7, pp. 4143-4153, 2024. https://doi.org/10.1007/s41870-024-01921-ydoi:[[[10.1007/s41870-024-0-y]]]
- 8 K. Agrawal and P. Sharma, "Symmetric-based cryptography key algorithm for data encryption and decryption in cloud computing," Journal of Advanced Engineering Research, vol. 10, no. 1, pp. 65-69, 2023.custom:[[[-]]]
- 9 K. C. Akshay, B. Muniyal, and V . Parashar, "Optimizing data retrieval for enhanced data integrity verification in cloud environments," Open Engineering, vol. 14, no. 1, article no. 20240058, 2024. https://doi.org/10. 1515/eng-2024-0058doi:[[[10.1515/eng--0058]]]
- 10 K. Lee, "Comments on "secure data sharing in cloud computing using revocable-storage identity-based encryption"," IEEE Transactions on Cloud Computing, vol. 8, no. 4, pp. 1299-1300, 2020. https://doi.org/ 10.1109/TCC.2020.2973623doi:[[[10.1109/TCC.2020.2973623]]]
- 11 S. Namasudra, "An improved attribute‐based encryption technique towards the data security in cloud computing," Concurrency and Computation: Practice and Experience, vol. 31, no. 3, article no. e4364, 2019. https://doi.org/10.1002/cpe.4364doi:[[[10.1002/cpe.4364]]]
- 12 M. Boussif, N. Aloui, and A. Cherif, "Secured cloud computing for medical data based on watermarking and encryption," IET Networks, vol. 7, no. 5, pp. 294-298, 2018. https://doi.org/10.1049/iet-net.2017.0180doi:[[[10.1049/iet-net.2017.0180]]]
- 13 H. Hong and Z. Sun, "Towards secure data sharing in cloud computing using attribute based proxy reencryption with keyword search," in Proceedings of 2017 IEEE 2nd International Conference on Cloud Computing and Big Data Analysis (ICCCBDA), Chengdu, China, 2017, pp. 218-223. https://doi.org/10.1109/ ICCCBDA.2017.7951914doi:[[[10.1109/ICCCBDA.2017.7951914]]]
- 14 Q. Huang, Y . Yang, and M. Shen, "Secure and efficient data collaboration with hierarchical attribute-based encryption in cloud computing," Future Generation Computer Systems, vol. 72, pp. 239-249, 2017. https://doi.org/10.1016/j.future.2016.09.021doi:[[[10.1016/j.future.2016.09.021]]]
- 15 S. Karthi, and S. Prabu, "Spatial data storage and retrieval in cloud computing environments using attribute based encryption algorithm," International Journal of Internet Technology and Secured Transactions, vol. 9, no. 1-2, pp. 163-183, 2019. https://doi.org/10.1504/IJITST.2019.098169doi:[[[10.1504/IJITST.2019.098169]]]
- 16 T. Bouabana-Tebibel and A. Kaci, "Parallel search over encrypted data under attribute based encryption on the cloud computing," Computers & Security, vol. 54, pp. 77-91, 2015. https://doi.org/10.1016/j.cose.2015. 04.007doi:[[[10.1016/j.cose.2015.04.007]]]
- 17 P. Sawle and T. Baraskar, "Survey on data classification and data encryption techniques used in cloud computing," International Journal of Computer Applications, vol. 135, no. 12, pp. 35-40, 2016. https://doi. org/10.5120/ijca2016908586doi:[[[10.5120/ijca908586]]]